Table of Contents
🛡️ Why March 2027 Matters
The Telecommunications Security Act (TSA) is the UK’s flagship cyber security regime for telecoms. It exists because telecoms networks now underpin critical national infrastructure and the wider economy, while threat levels have outgrown the old framework. The TSA sets mandatory minimum security standards for UK public network and service providers, with the Telecommunications Security Code of Practice spelling out what ‘good’ looks like in practice.
The requirements are phased between March 2024 and March 2028. The early waves in 2024 and 2025 focused on baseline hygiene that modern networks should already have in place. March 2027 is different. It’s where providers must show a clear uplift in operational maturity, including running functioning security capabilities across the network such as SIEM, 24/7 monitoring, proactive threat hunting, Privileged Access Management (PAM) and, for many, Privileged Access Workstations (PAWs). In short, the warm-up ends here. If you have not started building these capabilities, this is the year to move.
For a full TSA explainer covering the Act’s drivers, detailed scope rules, tiers, enforcement and earlier milestones, refer to our main TSA article.

👀 Who This Milestone Applies to (Tiers in Scope)
If you run a public electronic communications network (PECN) or service (PECS), the TSA applies to you. In practice this includes most of the UK telecoms ecosystem: mobile operators, broadband providers, ISPs, fibre network builders and managed service providers supporting telecoms networks.
Obligations scale through turnover-based tiering:
- Tier 1: £1 billion or more annual revenue
- Tier 2: £50 million to £1 billion
- Tier 3: under £50 million (but not a micro-entity)
Micro-entities are exempt from mandatory TSA measures.
Only micro-entities sit fully outside the TSA on paper. However, Tier 1 and Tier 2 providers must flow down TSA duties into their supply chain. That means smaller telcos, fibre start-ups or MSPs can still be pulled into TSA-aligned controls where they support a larger provider’s network or security-critical functions. If your service plugs into a bigger operator’s ecosystem, expect TSA expectations to follow.
🔄 What Should Already Be in Place (recap)
By now, early-phase TSA measures from March 2024 and March 2025 should be embedded. These controls are the platform for the heavier 2027 lift:
- Exposed edge and core protection
Clear visibility of externally facing systems, regular security testing and strong separation between the exposed edge and core so the edge cannot influence routing or deeper operations. - Hardened management plane
Privileged access logged, unique admin IDs, default credentials removed, secure management protocols in use, strong MFA for sensitive actions and tight oversight of third-party management access. - Signalling security and BGP controls
Understanding of signalling flows and processing elements, blocking spoofed or internal source addresses, monitoring and mitigating external BGP misuse, route filtering and minimising data exposed in signalling messages. - Supplier and third-party controls
Pre-contract risk assessments, end-of-life tracking, security testing evidence for equipment, contractual security expectations, secure data handling and logged, monitored third-party admin access. - CPE security
Unique device credentials, restricted management interfaces, secure protocols (eg TLS 1.2+), vendor support monitoring and default blocking of unsolicited inbound connections.
If these foundations are not stable, March 2027 becomes much harder to deliver and evidence. Full detail sits in our main TSA article.
March 2027 is the TSA step-change. If PAM, PAWs, SIEM/SOC and threat hunting aren’t already in build, you’re behind the curve.
🚀 March 2027 Requirements: What You Must Deliver
2026 is a deliberate breather in the TSA timeline, giving providers space to build the heavier operational capabilities required for March 2027. The diagram below shows how the TSA steps up from baseline controls into a full operational security model, with privileged access and monitoring as the core uplift areas.
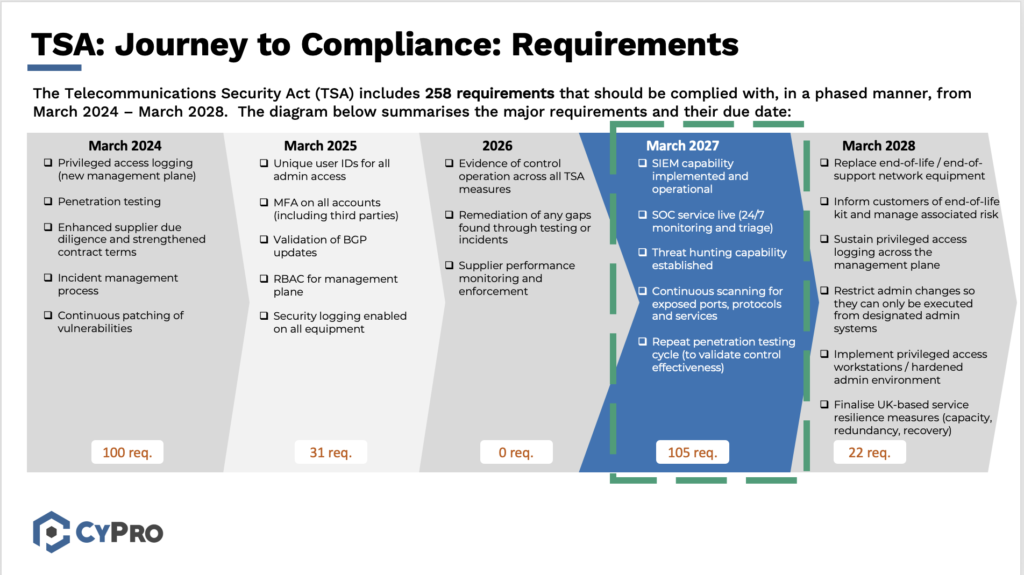
With that context, here’s what March 2027 requires in practice.
1. Privileged Access Management (PAM)
By March 2027, TSA becomes specific about privileged access in practice. Providers must demonstrate:
- A formal change process for operational changes except in genuine emergencies
- Secure storage of persistent and break-glass credentials protected by hardware means (eg TPM-based encryption, secure boot)
- Privileged access that is temporary, ticket-linked, time-bounded and automatically revoked through a PAM solution
- Fully recorded privileged management sessions
- Strong segregation between management segments, including third-party access
- Centralised element managers for privileged access rather than direct device logins
- No direct communication between managed elements over the management plane
- Oversight functions and MFA systems isolated from the corporate network
The direction is clear: ad-hoc, persistent or lightly governed privileged access has to disappear. Every privileged action must be traceable, justified and contained.
NTT Communications was breached via its internal Order Information Distribution System, exposing data for about 17,900 enterprise customers. This was a compromise of a security-critical management/orchestration platform. TSA’s 2027 PAM measures exist to stop that kind of admin-layer breach from becoming wider network control by forcing privileged access to be time-bound, ticketed, recorded and segregated.
2. Privileged Access Workstations (PAWs)
PAWs are dedicated, locked-down devices used only for privileged administrative work. By March 2027, telcos are expected to have these rolled out to anyone with elevated access.
A compliant PAW needs to be:
- Restricted only to the systems required for network changes
- Protected by hardware-backed encryption
- Patched rapidly, with security patches applied within 14 days
- Locked down with no corporate email, web browsing or productivity apps
- Controlled to block unapproved code from running
Getting PAWs right usually means changing day-to-day engineering rhythms: how access is granted, how troubleshooting happens and how changes are executed. Supply chain matters here too. Vendors and third-party administrators must use PAWs under flow-down obligations. A single PAW can access multiple customer environments where segregation and privileged-access rules are met.
Why this matters
Most privileged breaches start with mundane endpoint compromise (phishing, rogue extensions, unsafe networks or malicious attachments). From there, attackers harvest credentials and pivot into the management plane. PAWs remove that route by stripping admin endpoints back to hardened, purpose-built environments.
3. SOC, SIEM and threat intelligence
By March 2027, TSA expects providers to be running an operational security capability, not just collecting logs. The Act assumes a functioning SIEM, an operational SOC and proactive threat hunting supported by intelligence and behavioural telemetry.

SIEM requirements
Your SIEM must ingest and process logs in near real time (within five minutes). It should take in telemetry from:
- Network equipment
- Management plane systems (element managers, PAM platforms, orchestration, jump hosts, PAWs)
- Authentication and identity services
- Signalling systems (SS7, Diameter, GTP where applicable)
- Virtualisation fabric (hypervisors, hosts, orchestration and management layers)
- Oversight functions securing or controlling the network
The SIEM must provide:
- Enriched, correlated datasets with accurate time synchronisation
- 13-month retention for logs tied to security-critical functions
- Alerts when logs stop flowing
- Full audit trails for any log access, modification or deletion
SOC requirements
Whether in-house or outsourced, the SOC must support:
- Continuous 24×7 monitoring
- Detection of anomalous traffic, malicious behaviour and suspicious admin activity
- Analysis across different trust levels and network segments
- Escalation and resolution at pace
- Investigations using accurate asset, configuration and topology data
This is not a side-of-desk function. TSA expects analysts who understand telecoms networks, signalling, identity and virtualisation.
Threat intelligence and threat hunting
By 2027, providers must actively look for threats, not wait for alerts. TSA expects periodic threat hunting using network and host data, intelligence-driven searches for IOCs and TTPs relevant to telecoms, monitoring at trust-domain boundaries, enrichment with baselines of normal behaviour and automated config collection to detect unauthorised changes. Threat hunting can be delivered by a specialist third party, but TSA encourages avoiding conflicts where the same party operates the network and hunts it.
Why this matters
Telecoms networks are huge, distributed and constantly changing. Attack activity hides in subtle signalling anomalies, small BGP manipulations, unusual access patterns, compromised admin sessions and lateral movement inside virtualised workloads. Real-time monitoring and proactive hunting are the only scalable way to catch sophisticated actors before they become outages or breaches.
4. Signalling plane: active detection and protection
March 2027 is where signalling security moves from “understand the risk” to “defend it in real time”. Earlier waves expected providers to map signalling exposure and put baseline protections in place. The 2027 wave adds active, continuous control because signalling attacks do not need internal access to cause serious harm.
By March 2027, providers are expected to have:
- Continuous monitoring of inbound and outbound signalling traffic across externally facing interfaces, with detection tuned for telecoms-specific abuse patterns rather than generic network alerts.
- Protection of signalling records as sensitive data, with secure handling and access controls. Signalling logs and records can expose customer location, identifiers and network topology, so they must be treated like high-value operational data.
- Security analysis capable of spotting anomalous or malicious signalling behaviour, not just volume spikes. That includes patterns that suggest interception attempts, fraud, location tracking or disruption.
- Mechanisms to alert other providers about malicious signalling traffic, so abuse detected at your edge can be shared quickly across interconnects and roaming relationships.
- Detailed negative testing and fuzzing of externally exposed signalling interfaces, to prove that malformed, unexpected or hostile signalling messages cannot pass through and influence core functions.
Why this matters
Signalling weaknesses are a favourite route for hostile actors because they sit at trust boundaries and can be exploited remotely. A single weak signalling edge can allow interception, location tracking or disruption without the attacker ever touching your internal systems. The 2027 controls close the gap between earlier “baseline visibility” requirements and active defence, making signalling abuse something you detect, contain and evidence as part of steady-state operations.
5. Virtualisation security
For virtualised network functions, providers must show:
- Locked-down, up-to-date virtualisation fabric
- Secure host interfaces and restricted communication paths
- Hypervisors used for separation (containers not permitted for trust separation)
- Encryption at rest and in transit where required
- Signed workloads tied to a trust domain
- Oversight functions isolated in their own trusted environment
- Minimal privileged accounts for virtualisation admin
As networks become more software-defined, the hypervisor becomes the new core routing layer. TSA treats NFV as critical infrastructure, not “just another platform”.
Why this matters
Virtualisation concentrates risk. If the fabric, hypervisors, or management layer are compromised, attackers can pivot across multiple network functions at once, bypassing traditional perimeter controls. The 2027 measures are there to make sure the virtual layer is hardened, tightly segmented by trust domain, and monitored like any other security-critical part of the network, so a single NFV weakness cannot cascade into wider service disruption or loss of control.
6. Third-party lifecycle measures
March 2027 draws a hard line under legacy and supplier-driven risk. The TSA expectation is simple: security-critical functions should not rely on kit that vendors no longer support, because you cannot patch, harden or evidence control properly once support ends.
By March 2027 providers must show either:
- Unsupported or end-of-support equipment has already been replaced
- There is a clear, justified and tightly controlled plan to remove it in the very near term

If end-of-support kit remains, the bar is high: rare configuration changes, monitored exposed interfaces and minimal attack surface. In reality, replacement is the expectation, not the exception. Unsupported equipment is a reliable foothold for attackers once security updates stop.
Why this matters
This is a lifecycle and supply-chain control as much as a technical one. Providers need to know what kit is approaching end of support, sequence replacements early, and make sure suppliers are not quietly extending legacy dependencies across management, signalling, virtualisation or access layers. Unsupported equipment is a reliable foothold for attackers once updates stop, so the TSA position is clear: contain it briefly if you must, but replace it as the default.
💥 Business Impact: Cost, Risk and Upside
The March 2027 wave turns the TSA from a compliance programme into an operational test. This is the point where Ofcom expects to see security running in live networks at scale, not just planned on paper. That reality creates direct financial exposure, customer scrutiny and a clear performance gap between providers who are ready and those who are not.
Financial Exposure
Non-compliance can trigger fines of up to 10% of relevant turnover, plus daily penalties of up to £100,000 for continuing breaches. Because those caps scale with turnover, TSA risk grows with the size of the business. It is not a flat, absorbable compliance cost. What makes March 2027 higher-stakes than earlier waves is that the measures are operational by nature. If privileged access is still persistent or weakly governed, if hardened admin endpoints are not in place, or if monitoring and detection are not functioning across security-critical parts of the estate, that gap is visible through evidence and inspection and is enforceable.
Reputational and Customer Impact
By 2027, TSA alignment becomes something enterprise buyers and higher-tier operators assume you can demonstrate. The wave structure means customers can map what “good” should look like now: controlled privileged access, secure admin tooling, continuous monitoring with threat-led detection, resilient virtualised environments and a governed exit path for unsupported kit. If you cannot evidence those capabilities operating in steady state, it reads as a resilience weakness, not a minor audit shortfall. That affects renewal confidence, supplier assurance outcomes and how quickly you clear due diligence, especially where you support Tier 1 services through flow-down expectations.
Competitive Upside
Providers who treat March 2027 as an operating-model upgrade get a real commercial edge. Meeting the 2027 capability bar early means you can evidence mature privileged access, hardened admin activity and telecoms-grade monitoring without last-minute policy scrambles. In practice, that shortens customer assurance cycles, reduces friction in Tier 1 and public-sector supply chains and makes your security story repeatable for regulators and buyers. The TSA is designed to raise the sector baseline. If you are already there, you look like the safer, more reliable partner in a market where trust and uptime are everything.
Bottom line: March 2027 compliance reduces regulatory exposure and becomes a trust signal you can sell with. Treat it as a last-minute sprint and you risk fines and lost confidence at the same time.
In August 2025 Colt, a major UK network and telecoms services provider, suffered a ransomware attack that disrupted parts of its service estate. The incident underlines how quickly a compromise in operational systems can spill into live telecoms delivery, and why TSA’s 2027 wave pushes hard on PAM, PAWs and 24/7 monitoring to stop attacker controlled admin sessions turning into outages.
⚠️ Common Delivery Pitfalls to Avoid
Providers are running into a few repeat traps on the way to March 2027:
- Underestimating integration timelines
PAM, SIEM and ITSM integrations need mapping, process redesign, testing and tuning. None of it is plug-and-play, so late starts create bottlenecks. - Relying on legacy systems
Unsupported kit becomes a blocker when you introduce segmentation, PAWs and oversight controls. Replace or remove what cannot meet the standard. - Ignoring hidden costs
The spend is rarely just tools. Expect costs in onboarding, tuning, redesign, rollout, segmentation and the steady-state SOC operation. Budget early. - Using a generic IT provider as your SOC
Traditional MSP SOCs often lack telecoms-specific depth in signalling, NFV and privileged access. TSA monitoring requires domain expertise.
✅ March 2027 Readiness Checklist
STEP 1: Compliance Gap Analysis
- Identify capability gaps early
- Sequence delivery realistically (eg PAM → PAWs → SIEM/SOC → oversight)
- Decide what stays internal vs where specialist help is required
- Engage partners early for PAM, PAW or SIEM onboarding
STEP 2: Procurement and vendor due diligence
- Map which TSA duties flow down to each supplier
- Put the right security clauses into contracts
- Assess supplier maturity and evidence
- Identify any end-of-support kit in their stack that affects you
STEP 3: Internal vs external delivery decisions
- Be clear what must stay in-house
- Decide what can be delivered as a service
- Use specialists for complex one-off delivery work
- Consider ongoing services such as SOC, threat intel, threat hunting, vuln scanning and assurance
Treat March 2027 as an operating-model upgrade, not a last-minute compliance sprint. Start with privileged access and monitoring, then lock suppliers and evidence in parallel.
🔭 What Comes Next in March 2028 (preview)
After March 2027, the final March 2028 wave shifts from day-to-day operational security to tighter admin safeguards, signalling-edge hardening, end-to-end virtualisation fabric resilience, automated event prioritisation and UK-based service resilience and data location governance.
We will cover the full 2028 requirements separately.
For the full timeline view, see our main TSA article.
🎯 Closing Thoughts: Making TSA Compliance Stick
The TSA is a structural shift in how UK telecoms security is regulated and March 2027 is the proof point. Ofcom won’t be looking for intent or paperwork, it will be looking for live capability.
By the deadline you need PAM-controlled privileged access, PAWs for admin work, SOC/SIEM monitoring in steady state with threat-led detection and hunting, hardened virtualised environments and legacy risk either removed or on a governed exit path.
Providers need to act now to:
- Lock down what applies to you: map the March 2027 Code measures to your services, tier and suppliers.
- Build the core capabilities first: PAM, PAWs, SIEM/SOC maturity and threat hunting.
- Sort suppliers early: flow requirements into contracts where third parties touch critical functions.
- Evidence as you go: capture operational proof from day one, not at the deadline.
Handled properly, TSA readiness reduces regulatory risk and strengthens trust with customers and Tier 1 partners. For full TSA background and earlier milestones, see our main TSA article. If you want a quick roadmap sense-check, speak to a TSA expert.









