Table of Contents
🔗 Why True Innovation Depends on Cyber Resilience
Innovation without cyber resilience is like building a Formula 1 car without brakes, speed without control is a recipe for disaster. In today’s fast-paced technology landscape, trust is essential and your stakeholders expect security by default. Organisations that drive transformation must be the leaders in cyber maturity, not fall behind.
In the UK, half of businesses and a third of charities experienced a cyber breach in the past year, according to the UK Government Cyber Security Breaches Survey 2024. This underscores that resilience is no longer a luxury, but a baseline expectation.

Downtime, breaches, or non-compliance don’t just hurt operations – they stifle innovation. Incident response drains engineering capacity, while fines sap growth budgets. A study by Cockroach Labs found companies average 86 hours of downtime per year, yet only 20% feel prepared to respond. Meanwhile, IBM’s 2023 Cost of a Data Breach Report pegs the average breach at $4.88 million (£3.9 million).
Further academic research has found that organisations cut R&D spending by 10% following a breach, with a sustained drop in patent output. The innovation pipeline stalls while the organisation recovers.
Cyber resilience becomes the enabler: not just a shield but a framework that allows innovation to thrive.
🚀 Defining a Modern Cyber Resilience Strategy for High-Growth Innovators

Outdated cyber resilience strategies focused on backups and reactive policies are no longer fit for purpose. In 2025, modern resilience means building operational agility, system continuity and fast recovery directly into your tech and business stack:
- On-demand patching capabilities for your DevOps teams.
- End-to-end encryption for data in transit and at rest.
- Real-time breach detection and alerting mechanisms.
According to IBM’s 2023 Data Breach Report, companies with mature resilience programs save $1.76M (£1.4M) per incident.
A UK AdTech scale up, turned to CyPro to increase their cyber maturity as part of their enterprise growth strategy. With CyPro’s Virtual CISO service, they implemented a five-year security roadmap, established incident response plans and completed a rigorous cyber maturity assessment. By embedding resilience at a strategic level, they eliminated onboarding friction, accelerated compliance cycles and created the operational headroom needed for product innovation. Maturity didn’t slow them down—it gave them the confidence to move faster.
Secure Development as an Innovation Enabler
Security is often mislabelled as a blocker. In reality, security empowers development by reducing rework, accelerating compliance sign-off and embedding quality early:
DevSecOps practices that integrate code scanning and threat modelling into CI/CD – Gartner predicts that by 2028, 65% of organisations will adopt compliance automation in DevOps-reducing risk and improving lead times by at least 15%. Embedding tools like SAST/DAST into your CI/CD pipeline not only automates security checks, but also slashes manual handoffs, ensuring continuous compliance and freeing developer time.
Threat-informed development to limit regression bugs – According to a threat-modelling guide, defects caught during testing are 5x more expensive than those found in development, with fixes after deployment can cost 30x more. By embedding threat modelling early, teams reduce costly regressions, improve code quality and avoid late-stage security surprises.
Security artefact libraries that accelerate due diligence – The UK’s government “Secure by Design” artefact library offers reusable security patterns, threat models and blueprints-helping development teams ship with assurance, not overhead. Having ready-to-use security artefacts significantly speeds up enterprise due diligence, especially during mergers or new client onboarding.
Why does this matter for innovation? Because when developers are confident that their code won’t introduce vulnerabilities, they move faster. And when compliance teams trust the process, the reviews go quicker, too.
Secure development isn’t about slowing teams down – it’s about enabling innovation at scale. When security is built into the development lifecycle, it removes friction, accelerates delivery and gives teams the confidence to experiment and iterate. Instead of acting as a gatekeeper, security becomes the launchpad for faster, safer innovation.
💨 Shift Left, Move Fast: Injecting Security into Agile Innovation

Shift-left security more than just some trendy jargon. This strategy is about spotting and fixing issues early, rather than reacting late, which in turn lets security scale with speed. Embedding security into the early stages of development helps catch vulnerabilities before they hit production and keeps compliance lightweight. When teams embed security into their development lifecycle from the first planning session, they:
- Reduce the number of high-severity bugs caught in staging
- Avoid expensive last-minute security fixes
- Minimise disruption during audits and assessments
Key practices include;
- Static code analysis tools like SonarQube.
- Container and infrastructure scanning with tools like Checkov.
- Infrastructure as Code (IaC) misconfiguration detection and runtime security testing like Terrascan.
Automate security with CI/CD-integrated tools like Snyk, Fortify and Terraform Sentinel.
💪 Innovation in Action: How Resilient Startups Adopt Emerging Tech with Confidence
Adopting emerging tech can be seen as risky, but for resilient startups the risk is manageable. These organisations can run controlled pilots, build in security controls from day one and scale only after validation.
Using AI as an example, training large language models on sensitive datasets can pose GDPR challenges unless proper anonymisation and role-based access control are in place.
Resilient startups:
- Conduct data protection impact assessments before feature launches
- Partner with vCISOs to map technical controls to business strategy
- Use Cyber Essentials Plus as a stepping stone to ISO 27001
An example of this is CyPro’s work with as a Cyber Security Partner for a FinTech startup. With our support, they implemented a cyber resilience framework that enabled them to respond quickly to new client requirements, achieve fast compliance approvals and grow their enterprise customer base.
The Innovation-Resilience Feedback Loop
Every new tool, API, or cloud instance expands your attack surface. Resilience can absorb that complexity. Done well, it creates a golden loop:
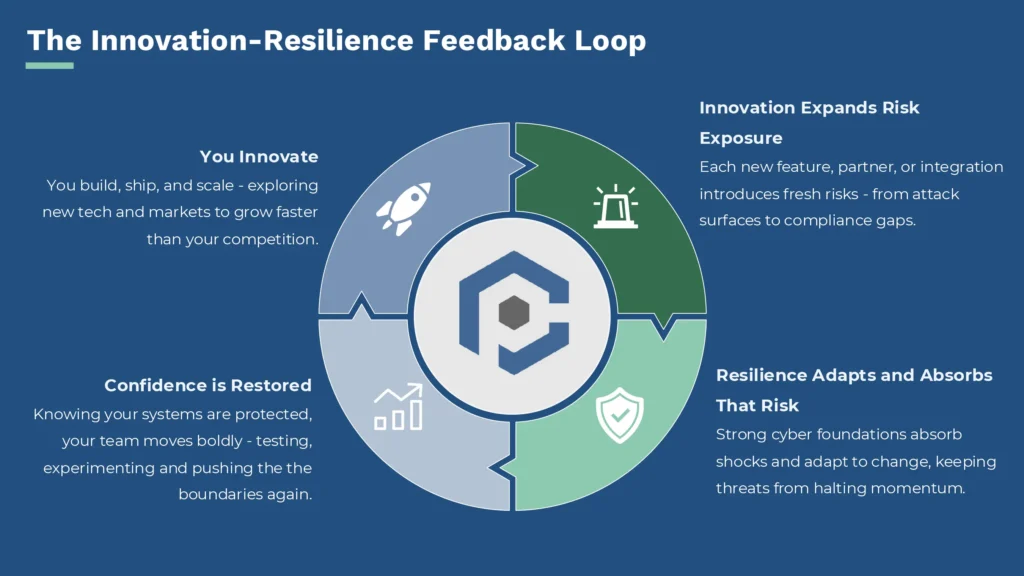
Perfection is not always what you need to strive for. The best methods revolve around cyber elasticity.
Cyber elasticity means your ability to bend but not break in the face of change, stress, or compromise. It’s about:
- Adapting to emerging threats without halting progress
- Recovering quickly from incidents without derailing operations
- Maintaining continuous security without blocking innovation
- Designing systems that evolve with your business, not against it
Ultimately, cyber elasticity enables organizations to absorb shock, adapt under pressure, and grow stronger with every challenge. That’s what turns resilience into a strategic advantage.
Want a north star? NIST’s Cybersecurity Framework 2.0 and the UK’s NCSC cyber resilience guidelines provide practical, scalable principles.
Innovation isn’t the enemy of security. In resilient organisations, they reinforce one another.
🧱 Build Your Resilience Strategy Around Innovation

Here’s your no-nonsense, battle-tested playbook:
Step 1: Start with a Cyber Capability Maturity Assessment
✅ Utilise our tool to baseline your current state.
Step 2: Map Cyber Security to Transformation Objectives
🎯 Align controls with your product roadmap. Launching in the US? Prep for SOC 2. Launching a new product? Nail ISO27001. Raising Series B? Align to the NIST CSF 2.0 framework.
Step 3: Bring in Strategic Oversight
👥 A Virtual CISO or Cyber-as-a-Service partner adds strategic rigour.
Step 4: Embed Secure-by-Design Culture
🧑💻 Train developers in threat modelling, privacy engineering and secure architecture.

Conclusion: Innovation Without Cyber Resilience Is Fragile
Innovation isn’t the opposite of security – they fuel each other. Without cyber resilience, you might launch fast, but when a breach hits or compliance gets in the way, you’ll wish you’d built stronger foundations.
💡 Resilience = Freedom to innovate.
It speeds up recovery, builds trust, and removes enterprise onboarding blockers. Most importantly, it gives your team the confidence to explore new tech without hesitation.
📥 Ready to grow securely?
👉 Contact CyPro’s experts today to get started.
Let’s make security a launchpad, not a roadblock.










