Table of Contents
🎯 About the Target
Organisation Profile (Size, Sector, IT Landscape)
The British Library cyber attack has become one of the most high-profile incidents in the UK’s public sector. The British Library is the UK’s national library and a major public institution, supporting millions of users annually across its sites in London and Yorkshire.
While globally recognised for its cultural importance, its underlying digital infrastructure was less secure and increasingly outdated, leaving it exposed to modern threats. This fragility became clear during the British Library cyber attack, which exposed the risks of relying on ageing systems.
| Number of Staff | Average of 1,581, excluding agency and contract staff |
| Sector | Public sector |
| Revenue | Annual revenue of £147.6m 2022-23 (Year ending 31 March 2023) |
| Services | Research access Digital archives Catalogues Public engagement Exhibitions Educational programmes Reading rooms |
| Founded | 1753 by Sir Hans Sloane |
| Ownership | UK Government |
| Funding | Publicly Funded by UK Government via the Department for Digital, Culture, Media and Sport (DCMS) |
Pre‑attack security posture
- Before the British Library cyber attack, the organisation’s cyber security posture was outdated and underfunded. It relied mainly on basic antivirus and firewalls, with no layered defence strategy.
- A remote access server introduced during the pandemic lacked multi-factor authentication (MFA), despite internal warnings.
- The IT estate was fragmented and heavily reliant on legacy systems, with patching inconsistent and system ownership unclear, leaving the organisation poorly prepared for the British Library cyber attack.
- Notably, when staff left, they often took undocumented knowledge with them, compounding the risks tied to an already fragile infrastructure.
- There was no evidence of prior ISO or Cyber Essentials certification, nor of a formally structured cyber security leadership team.
- The organisation faced the attack with poor governance, no defined cyber strategy, and a lack of in-house technical expertise, leaving it exposed to a complex threat like Ransomware.
🤔 Why They Were Targeted and By Whom?
Who Were the Attackers?
Understanding the nature of Rhysida is essential to grasp the scale of the British Library cyber attack. Rhysida is a ransomware-as-a-service (RaaS) group first identified in May 2023. Believed to be operated by Russian-speaking actors, the group runs an affiliate model, providing its malware to partners who carry out attacks in exchange for a share of the ransom. Rhysida is known for its double extortion tactics: encrypting victim systems and simultaneously exfiltrating data, threatening to publish it if a ransom isn’t paid.
Victims span critical sectors including education, healthcare, manufacturing, government, and IT. According to CISA and the FBI, Rhysida gains access via compromised credentials, often on systems without multi-factor authentication, and moves laterally using native tools like Remote Desktop Protocol (RDP) and PowerShell.
Strategic Appeal for Ransomware Groups
The British Library cyber attack illustrates why institutions like this appeal to ransomware groups. They look for organisations that:
- Have high public visibility, making disruption more impactful
- Lack advanced defences or modern detection systems
- Have limited incident response capacity
- Face budget constraints that delay security upgrades
For groups like Rhysida, this is the perfect environment: maximum leverage, minimum resistance.
Valuable data and weak defence
Rhysida is believed to have exploited a known weakness:
- Exposed remote access without multi-factor authentication (MFA)
- Specifically, the Terminal Services server installed in 2020, lacking MFA protection
This unprotected gateway:
- Allowed entry via credential-based attacks
- Enabled lateral movement and credential theft
- Played directly into double-extortion ransomware tactics
In short, the British Library cyber attack followed a proven attack playbook against a vulnerable target.
Who Else Have They Targeted?
The British Library cyber attack highlights why cultural and public institutions must invest in stronger cyber security.
Other Rhysida victims include:
- Education: Rutherford County Schools
- Healthcare: Prospect Medical, multiple U.S. providers
- Government: Chilean Army
- Transport: Seattle–Tacoma Airport
- Entertainment: Insomniac Games
- IT & Manufacturing: Various undisclosed organisations
These incidents show Rhysida’s reach spans multiple sectors and critical infrastructure.

⚡️What happened?
Understanding the Attack
The British Library cyber attack was a double-extortion ransomware assault: Rhysida extracted 600 GB of data (around 500,000 files) before encrypting systems and blocking operations until ransom demands were met. Following the refusal to pay the £600k ransom, the stolen data was leaked publicly, extending the British Library cyber attack far beyond initial disruption. The impact has persisted, with recovery efforts still ongoing in 2025.

What Type of Attack Was It?
This was a double-extortion ransomware attack, where attackers both encrypt a victim’s systems to block access and steal sensitive data to use as further leverage. The British Library cyber attack saw Rhysida encrypt critical systems and exfiltrate confidential files, threatening to release them publicly if a ransom wasn’t paid.
How Did They Execute the Attack?
The Library believes the attackers:
- Gained initial access by compromising privileged account credentials, likely through phishing, spear-phishing or brute-force attacks
- Escalated privileges and moved laterally using tools such as:
- PowerShell
- PsExec
- Cobalt Strike (blending in with normal system activity)
- Exfiltrated data using:
- FileZilla
- Rclone
- Deployed ransomware using ChaCha20 encryption wrapped with RSA keys
Victims were left with a CriticalBreachDetected.pdf ransom note and the threat of their stolen data appearing on Rhysida’s dark web leak site.
🔄 Attack Mechanism
MITRE Mapping
| Tactic | Technique | MITRE ID | Context in Rhysida Attacks |
| Initial Access | Valid Accounts (compromised credentials) | T1078 | First unauthorised access traced to Terminal Services, credentials likely stolen or bought |
| Initial Access | Phishing / Spear‑phishing | T1566 | Rhysida often phishes for credentials, matching the remote access breach |
| Execution | Command-line interface (PowerShell, etc.) | T1059 | Use of PowerShell observed for lateral movement and stealth in similar incidents |
| Defence Evasion | Clearing Event Logs | T1070.001 | Attackers removed system logs to frustrate forensic analysis |
| Lateral Movement | Remote Services (PsExec, RDP) | T1021 | Remote server used for lateral spread; PsExec likely used for internal navigation |
| Credential Access | Credential dumping | T1003.003 | Likely credential exfiltration during lateral movement phase |
| Discovery | Account & System Enumeration | T1087.002, T1016 | Attackers scanned network for HR, finance, and database assets |
| Collection / Exfiltration | Exfiltration over FTP or web (e.g. FileZilla, Rclone) | T1041 | Around 600 GB of data stolen using tools such as FileZilla or Rclone |
| Impact | Data Encrypted for Impact (ransomware) | T1486 | Files wiles encrypted with ChaCha20 & RSA, then nearly 500,000 files leaked publicly |
🕰️ Timeline of the British Library Cyber Attack
This timeline illustrates the key events and milestones in chronological order. It provides a clear view of how the situation unfolded, helping to contextualise the decisions, responses, and impacts over time.
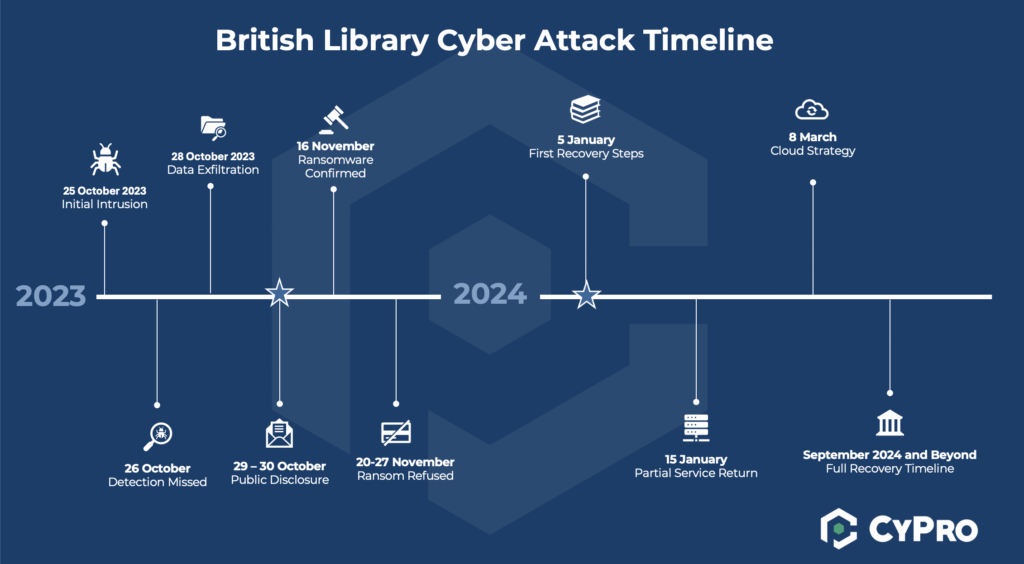
Initial Intrusion: 25 October 2023
At 23:29 on Wednesday 25 October, the British Library cyber attack began when Rhysida affiliates gained access to the network via the Terminal Services server. This remote access point, deployed in 2020, lacked multi-factor authentication and was regularly used by internal staff and trusted third-party contractors.
Within minutes, the attacker began moving laterally through the network using:
- Compromised credentials
- Admin-level access tools
These were early signs of hostile scanning that would later escalate into a full-scale breach.
Detection Missed: 26 October 2023
Just after midnight, the Library’s monitoring system automatically blocked suspicious behaviour. At 01:15, the IT Security Manager:
- Extended the block
- Ran a scan
- Checked logs
No further warning signs were found. The incident was escalated to the infrastructure team by 07:00, who reset the account and restored access later that day.
In hindsight, this early alert, triggered less than two hours after the British Library cyber attack began, was a missed opportunity to stop the breach before escalation.
Data Exfiltration: 28 October 2023
By 01:30am on Saturday 28 October, Jisc detected 440GB of outbound data traffic leaving the Library’s network. By this stage, the British Library cyber attack had escalated with the outbound traffic believed to be the set of internal files taken during the breach. Attackers used the following tools to extracted payroll data, HR records, contracts and full database backups:
- Robocopy
- SQLCMD
- FileZilla
- Rclone
Later that morning, users reported issues with Wi-Fi and library catalogue systems and technical degradation of network services that marked the start of a full compromise.
Public Disclosure: 29–31 October 2023
With critical systems offline, including:
- Website
- Catalogue
- Ticketing system
The Library publicly confirmed it was facing a cyber attack. At this point, the British Library cyber attack became widely known, as the NCSC was notified and external responders were engaged.
This transparency helped maintain public trust and accelerated incident response.
Ransomware Confirmed: 16 November 2023
Rhysida issued a ransom demand of 20 BTC (approx. £600k), threatening to leak stolen files if payment was refused.
When the Library declined, the British Library cyber attack intensified as attackers released nearly 500,000 documents on the dark web, increasing:
- Reputational risk
- Regulatory exposure
Ransom Refused: 20–27 November 2023
The Library stood by its decision to refuse payment despite further threats from Rhysida.
In retaliation, attackers continued releasing stolen documents, further damaging the Library’s public image and regulatory position.
Recovery Begins: 5 January 2024
The Library allocated £6–7 million from reserves to support recovery efforts, focusing on:
- Forensic analysis
- Emergency IT support
- Safe restoration of systems
The first step was launching a read-only version of the catalogue to support researchers and reduce disruption.
Partial Service Return: 15 January 2024
The catalogue was restored in a limited, read-only state, enabling:
- Basic record access
- Data integrity checks by technical teams
This cautious, phased restoration marked a turning point in the recovery process.
Cloud Strategy Announced: 8 March 2024
An official incident report outlined the attack and announced a strategic pivot to cloud-native infrastructure. This move aimed to improve:
- Incident response readiness
- Network segmentation
- Logging capabilities
Full Recovery Timeline: September 2024 and Beyond
Service restoration continued throughout 2024, including a £400k contract to rebuild the Library’s online estate.
While basic services returned, full recovery, including digital collections and resilience improvements, was still ongoing nearly two years later, underlining the long-term impact of unpatched vulnerabilities and legacy systems.
Containment and recovery are often underfunded, with too much emphasis placed on protective and detection capabilities. A cyber attack is inevitable; it’s a matter of when, not if. Prioritising investment in response and recovery delivers a far greater return on investment.
💥 Impact of the Cyber Attack
The impacts of the British Library cyber attack were not confined to IT systems; they affected services, people, and finances, as shown below.
| Types of Impact | Known Impact |
| Operational effects | Service Disruption |
| Financial consequences | £6-7 million in recovery costs |
| Reputational | Clear communication with public to maintain trust |
| Human / People Impacts | Personal data leaked |
| Ongoing Impacts | Full recovery yet to be completed |
| Supply Chain Disruption | ╳ |
| Regulatory / Legal Action | ╳ |
| Intellectual Property Loss | ╳ |
Operational effects
- Online catalogue, ticketing, Wi‑Fi and website were all taken offline.
- Researchers lost access to critical services like EThOS for several weeks.
- Reading rooms remained open but relied on slower manual processes.
- Core services were severely disrupted well into 2024.
- The incident exposed how the British Library cyber attack exposed deep reliance on outdated, fragile infrastructure.

Financial consequences
- Recovery cost estimated at £6–7 million, draining ~40% of reserves.
- Emergency spending covered forensics, infrastructure replacement and consultancy.
- Significant future investment needed to modernise IT systems.
- The British Library cyber attack turned into a long-term financial strain.
- Highlights how legacy systems can amplify the cost of an attack.
Reputational
- The transparency during the British Library cyber attack helped maintain public trust.
- Ongoing updates and NCSC collaboration were praised.
- Triggered broader discussion about cyber security in public services.
- Demonstrated that clear communication can protect reputation.
- Silence would likely have worsened stakeholder confidence.
Human / People Impacts
- Staff and user personal data was exposed on the dark web during the British Library cyber attack.
- The Library issued guidance and alerts in coordination with regulators.
- Individuals faced increased anxiety and identity fraud risk.
- Staff managed ongoing services while dealing with breach fallout.
- Internal pressure and public service responsibilities stretched teams thin.
Ongoing Impacts
- Remote ordering and manuscript access still limited by late 2024.
- Full cloud migration and security overhaul now underway in response to the British Library cyber attack.
- The recovery process proved lengthy and complex.
- Addressing legacy infrastructure required cultural and operational change.
- Cyber security is now embedded in executive-level decision-making.
💬 Professional Commentary
“One of the worst cyber incidents in British history’.” – Ciaran Martin, former CEO of the UK’s National Cyber Security Centre – The Guardian
This was not a minor disruption.
It was a complete compromise of a national institution’s digital backbone.
Systems were offline for months.
Staff data was dumped online.
Core public services were halted.
The scale of operational damage, financial cost and long-term recovery places this attack in a different league.
It exposed deep structural weaknesses and forced many organisations to reassess their own security posture.
“The attack was symptomatic of an under-resourced technical team and outsourcing of key infrastructure.” — Simon Bowie, former British Library systems librarian, LSE Impact of Social Sciences
When teams are stretched thin and underfunded, they become the weakest link in an organisation’s defence.
Outsourcing core systems can create gaps in coverage and accountability.
In the Library’s case, known security issues were not properly addressed.
This was not only a technical failure but a resourcing and structural one.
Without adequate investment in dedicated cyber expertise, even basic controls can fail.
“It is considered likely that the absence of MFA contributed to the attackers’ ability to enter the system via this route.” — The British Library
The lack of multi-factor authentication was a known vulnerability.
It had been identified in 2020 when MFA was rolled out elsewhere, but action here was delayed.
The Library admitted “the possible consequences were perhaps under-appraised”.
The gap remained open, providing the attackers with an entry point.
Identifying risks is not enough, in high-exposure organisations, implementation must be timely and mandatory.
⚖️ Comparative examples (Maersk’s NotPetya, Gloucester Council)
Flat networks, legacy infrastructure, and weak access controls are a common thread in some of the most damaging cyber attacks. When systems are not segmented or properly defended, a single compromise can spiral into widespread disruption, no matter the size or sector of the organisation.
The British Library cyber attack is not an isolated case. Similar structural weaknesses were seen in the following high-profile incidents:
- Maersk – Global disruption from poor segmentation
In June 2017, global shipping firm Maersk fell victim to the NotPetya malware. Although the infection began via compromised accounting software, Maersk’s flat, unsegmented IT network allowed the malware to spread rapidly. Within hours, the company lost access to 45,000 PCs, 4,000 servers and critical applications across 130 countries. Rebuilding from scratch cost Maersk an estimated £230 million and caused major global supply chain disruption. The attack underscored the dangers of technical debt and the importance of network isolation. - Gloucester City Council – Local shutdown triggered by email-based breach
In December 2021, a Conti ransomware attack on Gloucester City Council brought down services ranging from housing to council tax. The entry point was a phishing email, and outdated software meant recovery was painfully slow. Critical systems were offline for months, with a reported cost of over £1.1 million. The council also faced scrutiny from the Information Commissioner’s Office over delayed notification and security gaps. The attack revealed how even basic public services can grind to a halt without proper investment in cyber resilience. The British Library cyber attack underscores the same reality, showing how outdated systems make recovery painfully slow.
Like those incidents, the British Library cyber attack illustrates how outdated systems and poor segmentation can transform a single compromise into widespread disruption.

📚 What Can be Learnt?

Crucial Angles Often Overlooked
- Make Cyber Resilience a Priority – In a world where cyber attacks are inevitable for organisations like the British Library, investment must shift from protection and defence towards response and recovery capabilities.
- Test and Refine Your Response Under Realistic Conditions – An untested incident response plan can slow recovery. Regular exercises ensure teams make fast, confident decisions when real attacks hit.
- Act on Known Risks Before They’re Exploited – The lack of MFA on a remote access server was a known risk for the British Library which went unmitigated. Addressing such vulnerabilities early can prevent costly and prolonged disruption.
📋 Your Action Plan
1. Identify and prioritise key vulnerabilities
2. Enforce MFA on all critical systems
3. Minimise overprivileged access
4. Regularly test your incident response plan
5. Deliver phishing awareness training
6. Secure third-party access routes
7. Track attacker TTPs to inform defence


Final Thoughts
The British Library cyber attack remains one of the clearest demonstrations of how underfunded cyber security and outdated systems can expose a national institution. For public bodies and councils alike, the British Library cyber attack is a case study in why resilience, not complacency, must drive strategy.
Worried about your organisation’s ability to respond to an attack or defend against evolving threats? Don’t leave yourself exposed. Contact CyPro today to assess your vulnerabilities, strengthen your defences, and take control of your cyber security posture before you face a crisis like the British Library cyber attack.










