Table of Contents
📉 Why Traditional Penetration Testing is Now a Commodity
Penetration testing has drifted far from its original purpose. Once a valuable tool in the defender’s arsenal, today’s typical penetration test is too often seen as a commoditised checkbox exercise. Instead of improving resilience, a penetration test is now usually mandated by compliance frameworks and delivered by vendors more focused on maximising margin than genuine security value.
The problem? A transactional mindset that has limited coverage, incomplete view of risk and delivers templated and generic reports rather than uncovering genuine business risks.
The Compliance-only Mindset
Many organisations no longer view penetration tests as a way to improve security posture. Instead, they’re a mandatory line item driven by client requirements, auditors or board members. Tick the box. Move on. A penetration test in this context becomes paperwork, not protection. Repeating the same penetration test year after year only reinforces the problem.
Penetration tests can only focus only on ‘stuff’ they are pointed at. If you don’t tell the tester to check an area, it gets ignored. The classic ‘you don’t know what you don’t know’. That narrow focus ignores how real-world attackers work and leaves many vulnerabilities open, undetected. A penetration test that’s too narrowly defined offers only a false comfort blanket and risks creating dangerous blind spots.
Penetration testing is good for ticking compliance boxes but not for discovery and reducing an organisations complete attack surface.
🫣 You Can’t Secure What You Can’t See
Most penetration tests completely miss vast swathes of the modern attack surface. With growing cloud adoption, shadow IT, complex identity estates and increasingly complex hybrid networks, companies are more exposed than ever. Traditional penetration tests can only look at the scope they are bounded by, which is why a single penetration test is never enough for organisations with evolving attack surfaces.
How Hackers Actually Operate
Unlike pen testers who operate within scoped boundaries, attackers aren’t limited by your engagement brief. They explore all possible external, internal, people-based and supply chain vectors, using thorough reconnaissance and lateral movement techniques. This difference exposes the gap between a penetration test and how a real-world adversary operates, and why a penetration test can never replicate the full scope of an attacker.
A CyPro-led exercise uncovered unsecured sensitive documents in exposed AWS buckets that were not included in the original pen test scope. These were flagged by attackers on dark web forums.
🔄 The First Evolution: From Pen Testing to Attack Surface Assessment
Penetration testing will always remain a necessity but for those seeking a complete view of their organisation’s attack surface, the industry’s response to these limitations was the attack surface assessment (ASA). ASAs promised broader visibility, looking beyond the network perimeter.
Recognising this limitation, regulatory frameworks began to adapt. One of the most notable examples is CBEST, the Bank of England’s intelligence-led red teaming framework for financial institutions. CBEST moved beyond traditional pen testing by mandating threat intelligence-led reconnaissance and attack surface mapping as formal components of its assessments. The introduction of these requirements helped shift focus away from scoped engagements and towards real-world adversary simulation.
In practical terms, CBEST engagements begin with reconnaissance and threat intelligence gathering, often identifying key assets and systems that would not have been tested under conventional penetration test scopes. Unlike a standard penetration test, this process ensures red team activities reflect how a real attacker might target the institution, not just what the client happens to know or disclose. The result is a more holistic view of risk that better informs executive-level risk decisions and resilience planning.
While a step in the right direction, these assessments are still fundamentally flawed. Conventional Attack Surface Assessments are still marred with challenges.
🐶 The Tail Wagging The Dog: Tool-driven Approaches

Most vendors lead with their favourite technology first, not the client’s needs. They scope the work around the tool’s capabilities, limiting coverage to just one layer of the attack surface, unable to report on the total attack surface for an organisation:
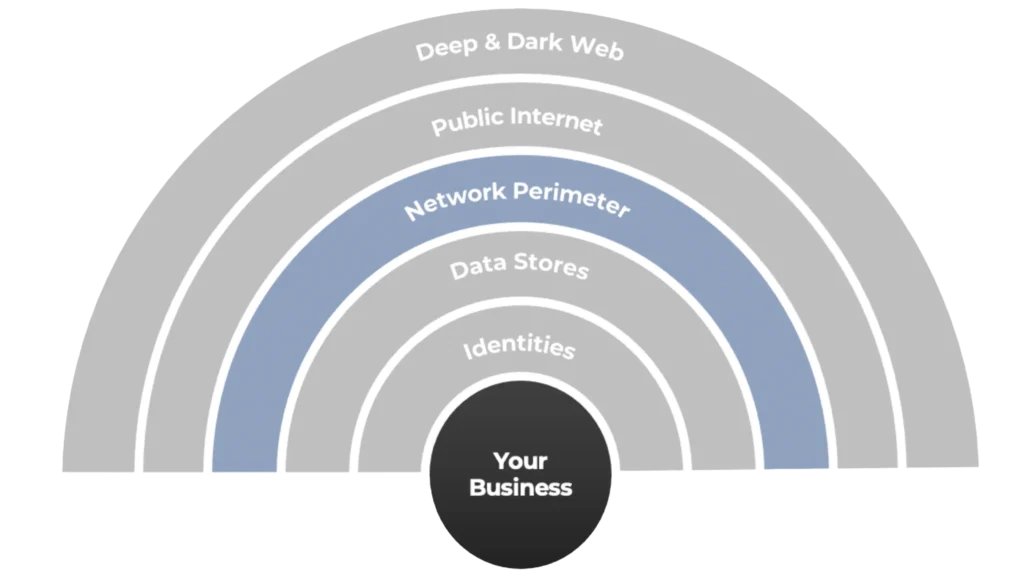
Automated scanning tools are technologically limited. They typically are only able to focus on one or maximum two layers of the attack surface.
This is a great example of allowing the “tail to wag the dog”. The selection of a technology is allowed to determine the scope of the testing, not the other way round. One should determine the scope of a test and then select the technologies that enable that scope to be executed. Only that way does one get a true view of the total risk.
The Fog of False Positives
Vendors want to show they’ve found something and so too many ASAs overwhelm clients with vulnerabilities that are technically valid but irrelevant in the wider business context.
Traditional attack surface assessments generate thousands of issues with little context. Reports are often unreadable for leadership and are too dense for busy IT teams to action effectively. They remain focused on technical vulnerabilities, not visibility of total attack surface.
For example, you might have a critical vulnerability on an exposed internet facing asset but due to the way it connects to internal systems it is entirely un-exploitable.
A CyPro client received a 100-page ASA report from a vendor that highlighted over 3,000 issues. However, 95% were low-risk or false positives. No prioritisation. No context. Result: analysis paralysis.
This is leading to the advent of what we like to call Attack Surface Testing.
Thousands of scan results do not equal better security. Context is king.
🚀 The Second Evolution: From Attack Surface Assessment to Attack Surface Testing
The next evolution? Attack surface testing (AST).
Unlike tool-led approaches that conventional attack surface assessments bring, which prioritise vendor margins, AST is a bespoke, service-led methodology that blends human-led threat hunting with full attack surface discovery.
The Full Attack Surface: What Most Assessments Miss
Most assessments only scratch the surface of digital risk. They focus on external perimeters while ignoring internal threats, identity sprawl and data leaks on the dark web. AST provides holistic coverage across five key domains:
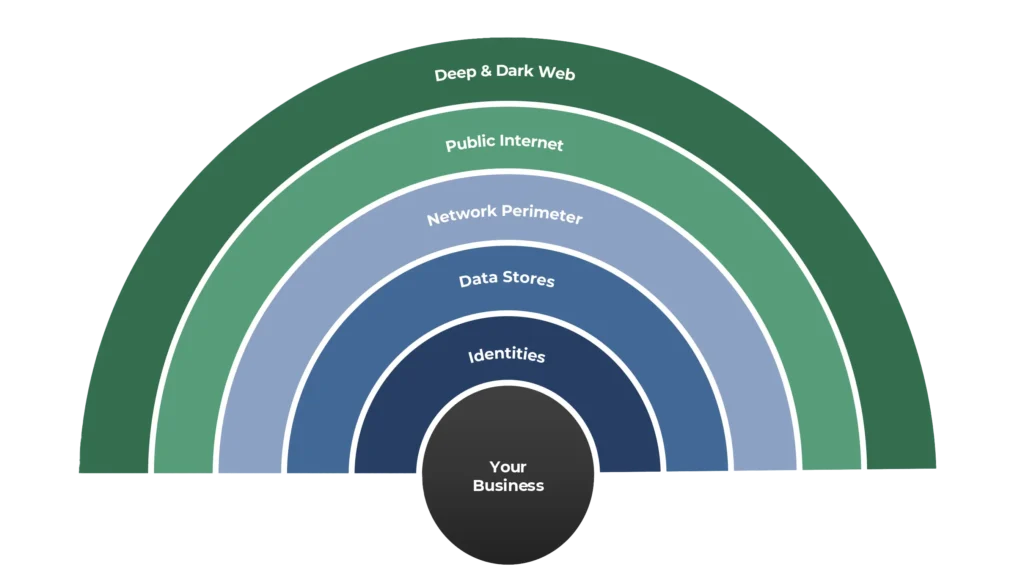
1. Deep and Dark Web
Monitoring non-indexed web spaces for leaked credentials, breached data, and adversarial chatter about your organisation. This includes deep web sources such as private forums and subscription-based breach databases, as well as dark web marketplaces, IRC channels, and sites accessible via Tor. For example, credentials from a 2023 HR system breach at a UK-based fintech firm were found on a darknet leak site two weeks before any breach was disclosed, alerting the client to take immediate defensive actions.
2. Public Internet
This domain covers indexed content available on the open web through search engines like Google, Bing and Yahoo.
It includes exposed cloud buckets (e.g. AWS S3 with public access), mistakenly shared HR policy PDFs, configuration files left in GitHub repos, or staff profiles on career pages exposing tech stack intel.
3. Network Perimeter
Encompasses internet-facing assets such as open ports, web servers, VPN gateways and other boundary infrastructure.
This is where traditional pen testing focuses, scanning for common vulnerabilities, outdated software and default credentials. However, many tests fail to correlate findings across assets.
4. Data Stores
Internal repositories, including SharePoint, OneDrive, NAS drives and Dropbox environments, often hold high-value unstructured data such as customer files, business plans and employee PII. These stores frequently suffer from ‘permission creep’, where access expands over time without formal review. A recent AST uncovered 3,200 sensitive files on a legacy SharePoint drive that was accessible to all UK employees, including the marketing interns.
5. Identities
User and system identities, especially those left behind after staff departures or role changes, present a major risk. Dormant admin accounts, hardcoded credentials in CI/CD pipelines and cloud IAM (Identity and Access Management) roles with excessive permissions are often used by attackers to gain or maintain access. In one engagement, AST uncovered over 150 dormant Azure AD accounts, one of which had MFA disabled and global admin privileges.
⚖️ Comparison Table: Typical ASA vs Attack Surface Testing
| Domain | Traditional ASA | Attack Surface Testing |
| Deep/Dark Web | ❌ | ✅ |
| Public Internet | ❌ | ✅ |
| Network Perimeter | ✅ | ✅ |
| Data Stores | ❌ | ✅ |
| Identities | ❌ | ✅ |
🏆 A New Service-Led Approach: Attack Surface Testing
Shift Away From Simple Tools
“The scanner said it was clean.”
Yeah, they all do.
What automated tools don’t see is often where the biggest risks hide. AST is led by analysts who don’t just run scans, they think. They explore. They ask: “What’s missing?”
One client, a financial consultancy, had a legacy FTP server sat quietly online. It hadn’t been used in years. It also hadn’t been turned off. Automated tooling ignored it. A human didn’t, they found it hosting sensitive documentation, fully exposed.
Complete View of Digital Exposure
AST considers not just the edge of the network, but the entire ecosystem where digital exposure occurs: cloud infrastructure, shadow IT, leaked credentials, misconfigured storage and identity sprawl. Let’s get this straight: the perimeter is dead.
AST takes into account:
- Shadow IT and forgotten SaaS tools
- Poorly decommissioned cloud storage
- Misconfigured internal apps left externally accessible
- Credentials floating around in the wild
At a property firm, we uncovered three ancient partner portals, all still accessible, and all indexed by public search. They contained old documentation, test environments and internal links. None of it was in scope for traditional vuln tools, but it was very much in scope for an attacker.
One example involved a property management firm whose AST revealed three external partner portals hosting outdated documentation and test environments that had never been decommissioned. These had been ignored by vulnerability tools but were discovered through manual link mapping and open-source intelligence (OSINT).
Focus on Lifetime Value, Not Margin
Some services aim for high-margin delivery. AST doesn’t.
Rather than a transactional engagement designed to maximise short-term profit, AST is usually offered as a subsidised or value-based service aimed at forming a long-term security partnership.
One UK logistics company used AST as their first engagement with CyPro, which later matured into a managed detection and response (MDR) relationship. The initial subsidised AST helped identify risks and gain executive buy-in for future security investments.
At CyPro, we often run AST as a subsidised or break-even engagement. Why? Because it opens doors.
Short-term margin? Sacrificed.
Long-term relationship? Established
Experts Mimic Real Attacker Reconnaissance

Let’s say this bluntly: real attackers don’t start with Nessus.
Human-led AST teams think like adversaries. They examine external mentions, look for OSINT trails, scrape social media metadata, probe DNS history and explore forgotten subdomains. Attackers start with breadcrumbs:
- Old subdomains
- DNS history
- Open buckets
- Leaky JavaScript
- OSINT in LinkedIn job posts
One of our analysts found internal file paths in a marketing JS file. It exposed folder structure, naming conventions, and environment links. Nobody would’ve spotted that without scraping the front-end manually. For example, a threat hunter at CyPro discovered internal file paths accidentally exposed on a marketing subdomain due to a misconfigured JavaScript file. The information within could have been used by a real attacker to identify internal directory structures and plan lateral movement.
Human-led Threat Recon & Contextualisation
Let’s kill the CVSS obsession.
A printer management system had an RCE. Sounded scary.
But it was behind a jump box. Access required VPN and MFA.
So in context? Low-risk.
Meanwhile, a cloud IAM policy was misconfigured and gave wide access to customer PII with no MFA enforcement. No flashy CVSS score. High-risk.
This is why AST isn’t just about what’s technically vulnerable, it’s about what’s practically exploitable and operationally dangerous.
CXO-Level Outputs
AST reporting is built for multi-audience impact. Executive-level summaries highlight strategic risk in plain language while technical annexes provide actionable detail for engineers. In one case, a scale-up’s CFO cited the AST report directly during a board meeting to justify a budget increase for IAM overhaul. That level of clarity and relevance makes security a board-level conversation rather than just a technical side note.
One of the most underrated outcomes of AST? Executives understand it.
Why? Because AST reports aren’t just tech dumps. They’re structured:
- Up top: business risk in human language
- In the middle: attack chains and likelihood
- At the bottom: technical detail for the engineers
A CFO from a SaaS scale-up literally quoted the AST report at the board to argue for budget. He won. That’s what happens when security reporting stops being a PDF full of CVEs and starts telling a story people actually get.
If your board can’t understand your security report, it’s not a useful report.
💎 Why This Approach Delivers More Business Value to Clients
Significant and Rapid Risk Reduction
With a broader scope and human-led contextualisation, AST identifies and helps close genuine exposures at a fast pace. For example, a financial services client discovered their HR system was publicly exposed due to misconfigured DNS entries, something no vulnerability scanner had detected. The issue was remediated within 24 hours of AST discovery, preventing a potential breach that could have led to FCA (Financial Conduct Authority) scrutiny and reputational damage.
Decrease Total Cost of Ownership
Fixing vulnerabilities during the reconnaissance phase is significantly cheaper than responding post-breach. In one instance, a manufacturing client used AST to uncover unpatched devices in a forgotten business unit. Remediating these before an exploit avoided what could have been a six-figure ransomware incident. The ROI (Return on Investment) was measured not only in cost avoidance, but in retained business continuity.
Reduce Microsoft Licensing Costs
AST commonly reveals accounts that have not logged in for 6+ months but still carry enterprise-level Microsoft licences. For example, a mid-sized UK law firm recovered over £18,000 annually by deactivating and de-licensing unused Microsoft 365 accounts following AST analysis of their Azure AD environment.
Reduce Cloud Hosting Costs
Attack surface testing isn’t just about improving your security posture, it can also uncover significant savings in your cloud bill. By mapping everything that’s publicly exposed, it often reveals cloud resources that are unnecessary, forgotten or poorly configured.
Key ways it reduces cloud hosting costs:
- Unused assets: Identifies orphaned VMs, storage, load balancers and IPs still running (and billing) long after their use has ended.
- Over-provisioning: Highlights oversized compute resources or services that are costing more than they need to for their actual usage.
- Poor design: Exposes architectural inefficiencies like multiple public gateways or unnecessary cross-region deployments.
- Shadow IT: Finds unmanaged, untracked deployments that teams have spun up outside formal change control and cost visibility.
- Tagging and hygiene: Encourages better resource tagging and lifecycle management, making it easier to monitor, charge back, and decommission.
Ultimately, it’s a way to improve both risk posture and operational efficiency. Done well, attack surface testing can pay for itself, not just in avoided breaches, but in hard savings too.
AST regularly identifies workloads left running in AWS, GCP or Azure that no longer serve a purpose. In a recent CyPro engagement, a retail brand identified 47 orphaned cloud assets, some of which had been incurring storage and compute costs for years. By consolidating these assets, the brand saved over £12,000 per annum.
Identify Inefficient Business Processes
Legacy access controls often reveal process inefficiencies. During one AST engagement, a healthcare provider’s Joiner-Mover-Leaver (JML) process was found to be non-functional: ex-employees retained VPN access for up to 18 months post-departure.
Not only was this a critical security gap, but it indicated a broken HR-IT process handoff. Fixing the root cause improved both security and organisational efficiency.
🎯 Conclusion
Traditional penetration testing alone no longer serves modern businesses. It ticks boxes but fails to reflect how attackers think or act. Even though attack surface assessments provide a broad overview, they have now shown their limitations by lacking essential context. A penetration test may tick the compliance box, but only attack surface testing provides real protection.
Attack surface testing is the answer: a full-spectrum, human-led service that delivers real insight and real protection.
👉 Contact CyPro today to see your attack surface the way attackers do.
💬 FAQ
What is an attack surface assessment vs penetration test?
Pen testing targets specific areas of a system for vulnerabilities, usually defined by scope. A penetration test can reveal weaknesses in the chosen environment, but it won’t show the full picture. By contrast, an attack surface assessment looks more broadly at what’s visible externally, though it is often limited to automated scans.
How to choose a quality attack surface assessment provider?
Look for providers that use human analysts alongside tooling, offer contextualised reports and cover all five layers of the attack surface, not just your network perimeter.
How often should I do an attack surface assessment?
At least quarterly, or whenever major architectural or operational changes are made (e.g. new acquisitions, product launches, migrations). In between, a penetration test may still be required for compliance or targeted validation, but it should not be your only line of assurance.
What’s the cost of a service-led model vs tool-only?
Tool-only assessments can cost as little as £2,000–£5,000 but deliver limited value. Service-led ASTs may range from £5,000–£20,000 depending on scope, but with significantly more impact and long-term ROI. The commercial savings from a service based approach can be up to 4-5 times the original cost of the AST exercise.
News and Updates
October 2025
- Cyber incidents have continued to rise across the UK, with the NCSC’s Annual Review 2025 revealing that serious attacks have doubled in the past year and calling on organisations to adopt continuous validation and real-time monitoring to strengthen defences.
- Microsoft Security echoed this warning later in the month, releasing new insights that stressed the importance of ongoing visibility and adaptive testing to stay ahead of fast-moving threats.
- This growing alignment between government and industry shows that traditional, one-off penetration testing is rapidly being replaced by continuous exposure management, as organisations move to close the gaps attackers exploit between test cycles.