By a UK based cyber security specialist who has spent the last decade translating hacker tactics into board-ready language.
Table of Contents
📌 Featured summary for skimmers
- Traditional “one-off” attack surface assessments might give network defenders a warm fuzzy feeling, but like many basic attack surface assessments they often offer a false sense of security.
- By the time the hefty PDF report lands on your desk and you’ve deciphered what the reams of technical data means, a ransomware crew has already plotted an efficient path of attack, straight to the heart of your critical assets.
In this article we explore how a modern, regular, attacker-aligned assessment (covering all elements of the attack surface) can turn technical noise into business-ready, actionable, risk insight.
A good assessment is less about counting vulnerabilities and more about showing which two or three combined issues can grant an attacker access to your most sensitive systems.
🌐 What is An Attack Surface?
An organisation’s attack surface is the sum of every place, digital or human, where a threat actor could gain a foothold in order to launch an attack against your organisation. It is made up of five intertwined elements:
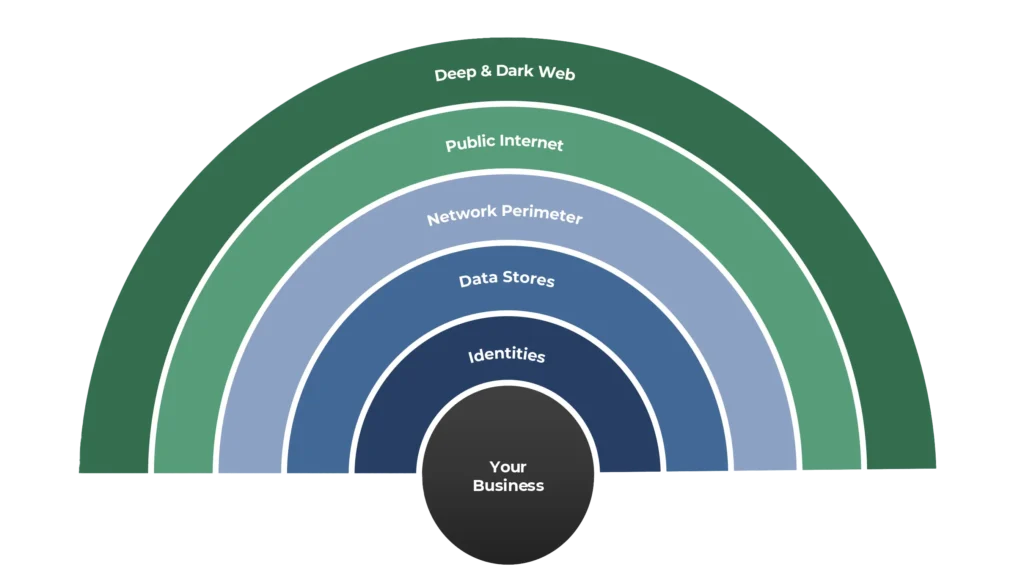
Deep & Dark Web: Hidden, anonymous networks where stolen credentials and sensitive company data are bought and sold on criminal forums, offering attackers an easy means of planning their attack.
Public Internet: A broad source of a wide variety of valuable information from GitHub code snippets to LinkedIn job posts containing information about company systems and staff contact details which attackers can use to craft convincing phishing scams.
Network perimeter: Your web facing environment, made up of web servers, VPN gateways, cloud endpoints, login pages and open ports which provides technical points of entry when misconfigured or left unpatched.
Data Stores: Your cloud environment (be it Google Drive, Microsoft 365 or something else) might be the secure vault in which you store all your company’s data. But if everyone in the organisation (including your guest users) have access to that data then there’s a risk of sensitive information inadvertently being shared too permissively and ending up in the wrong hands or users accumulating group memberships like Pokemon cards (gotta catch ‘em all, right?)
Identities: The most often overlooked layer of the attack surface, consisting of employee accounts, disabled but not deleted admin accounts and service tokens that have the potential to allow an attacker to move through your network and execute commands once they are inside the walls.
Together these five zones form a single, shifting map; defending it means monitoring all of them in concert rather than treating each in isolation. A thorough attack surface assessment should map across all five, not just one or two.

🖼️ The Big Picture: Attack Surface vs Vulnerability Assessment
Think of your organisation as a stately home, full of valuable treasures that might catch the attention of a nefarious gang of thieves.

A classic vulnerability scan measures how sturdy each door is (by giving it a good rattle). In comparison, an attack surface assessment counts every door, skylight, tradesman’s entrance and unearths that forgotten Instagram post that mentions which flowerpot the spare key is hidden under.
In cyber security terms it replicates the reconnaissance activities undertaken by a threat actor before they launch an attack and attempts to identify weaknesses (such as shadow IT, open ports, retired login pages and leaked credentials) that can help an actor infiltrate your environment without being spotted.
🤕 Traditional Assessments Points
Limited Scope
A traditional penetration test focuses only on the system or asset in scope and will not exceed that. That’s brilliant, if you want to really understand the security weaknesses in that area, but it doesn’t give you a broader sense of how your organisation would stand up to the scrutiny of a motivated threat actor. It also means that an organisation may not have a true appreciation of the scope of their attack surface, something a traditional attack surface assessment often fails to uncover. You can’t secure what you can’t see.
Technology Driven Approach
Many organisations approach this from a ‘technology first’ standpoint. What this means is, they look first at what technology and security tools they have available and then see what it can tell them about their organisation.
This means that the organisation only sees the threat that is in scope of their toolset, rather than determining what the potential threats to the organisation are, then determining which tools a threat actor might use identify them.
False Positives
Traditional assessments often deliver findings in a hefty PDF, or worse, as CSV output direct from the analyst’s tool of choice. The belief that ‘more is better’ means every issue is listed however small leading to an over-reporting of false positives. While this makes the report look impressively chunky, it can lessen value as readers struggle to find relevant areas for risk reduction among the noise. Poorly executed attack surface assessments often add to this noise by flooding teams with irrelevant findings.
Technical Findings
Direct from tool reports are generally highly technical in nature, with each finding is presented and analysed independently with little consideration as to how they might be linked together by an attacker to develop a rapid and effective means of attack. This means they fail to provide organisations with an understanding of the business benefits of remediation, and traditional attack surface assessments often suffer from the same limitation.
Number of findings is not a measure of success; the ability to take proactive steps to block an attacker’s route into your organisation is.
⚖️ Approach Comparison
| Benefit | Penetration Testing | Traditional Attack Surface Assessment | Vulnerability Scanning | Attack Surface Reduction |
| Targeted Control Assurance | ✅ | ✅ | ✅ | ✅ |
| Compliance (ISO, SOC2, PCI, DORA) | ✅ | ✅ | ✅ | ✅ |
| Reduce overall attack surface | ❌ | ❌ | ❌ | ✅ |
| Decrease total cost of ownership | ❌ | ❌ | ❌ | ✅ |
| Reduce licensing costs | ❌ | ❌ | ❌ | ✅ |
| Reduce hosting costs | ❌ | ❌ | ❌ | ✅ |
| Identify inefficient business processes | ❌ | ❌ | ❌ | ✅ |
👀 What Do CISOs Actually Want to See?
The overuse of heavy technical content in traditional reporting means that attack surface assessment reports often stay in the hands of technical teams, meaning that executives don’t have visibility of the potential risk reduction that could be achieved. COOs and CISOs are not looking for a port-scan output to solve their security issues; they green-light budgetary spend for outputs that:
- Reduce the probability of expensive incidents: the UK Government’s 2025 Cyber Breaches Survey shows 43% of firms still get hit each year and the average disruptive breach now costs £3,550 (gov.uk).
- Early visibility of potential threats and vulnerabilities specifically relevant to their sector and organisation: a retailer may be more concerned about vulnerabilities that have the potential to affect their supply chain systems, while a healthcare provider fears the public disclosure of sensitive personal information and the fines that this can incur.
- Clear priorities for limited resources: Very few organisations have the time or resources to evaluate and fix 2,000 unrelated findings, but everyone can prioritise the five fixes that will collapse an attack chain.
- Manage Costs: Organisations often spend additional money on services that are no longer required. Promptly identifying accounts and data that is no longer required can have a positive impact on the organisation’s bottom line.
When an attack surface assessment fails to translate technical chatter into those business outcomes it will not be read, used or performed a second time.

🚨 1, 2, 3… Breach
Most real-world compromises follow a core sequence of events, that are summarised below:
- Scoping the Target – Attackers use an array of tools to gather information about their target from the internet, social media, the dark web and the company itself. They often do so passively, so as not to arouse the suspicions of cyber defenders.
- Getting a Foot in the Door – Attackers use the information gathered to gain access to their target. This could be by through many means, including exploitation of un-patched VPNs or using credentials that have been leaked on the dark web. Attackers looking to deploy malware may deliver their payload to their intended target. Using information gathered in reconnaissance helps focus this, for example they could use LinkedIn to find the email address of a Systems Administrator with privileged access or could identify a public facing cloud server where malware can be drop.
- Moving to Critical Systems – Attackers may be able to move across the network by pivoting from identified, public-facing file shares, to internal systems which shouldn’t be accessed.
In spring 2025 the hacking group Scattered Spider were able to compromise the network of retail giant M&S causing the company to lose an estimated £300 million from profit projections. The reported route of entry? User credentials stolen from a trusted-third party (BBC).
🔐 3 Steps to Enhanced Security
To align our assessment to the behaviour of an attacker, we must think like an attacker, rather than a defender:

Step 1 – The Right Toolset, The Right Scope
Attackers use a range of tools in conducting reconnaissance – not just one. We deploy a curated set of tools, both open source and commercial, to replicate those used in attack planning. This gives us a comprehensive view of all layers of the attack surface, rather than the traditional one or two.
Step 2 – Check and Validate
We use highly-experienced human analysts to confirm results and assess their specific relevance to you, significantly reducing the number of false positive findings.
Step 3 – Enrichment and Modelling
Analysts assess the findings in relation to each other and develop storyboards to demonstrate how findings can be used in concert to successfully conduct an attack. These are clear and understandable narratives designed to be understood by non-technical audiences.
The ransomware gang INC Ransom stole 1.3 TB of data on Leicestershire residents, after identifying and accessing an unused VPN account which did not have multi-factor authentication enabled. Subsequent reports from the council confirmed that confidential information was then published online. How could this have been avoided? Proactive identification of orphaned accounts through identity management.
🔗 When Two Lows Make a Critical: The Power of Attack Chains
Picture three innocuous, and (at first glance) unrelated findings, several hundred rows apart from each other in a bog-standard vulnerability assessment report:
- login.acme-erp.com website which shows a generic login splash page
- A pastebin dump, available to find through a search engine, which contains a list of usernames and passwords including: jsmith@acme.com : Summer2023!.
- A LinkedIn profile for a John Smith which boasts that his current role is “ERP administrator, ACME”.
Individually each looks low risk and probably will find itself near the bottom of the remediation list. But together they offer attackers a ready-made brute-force path into a high-privilege portal, something that may not have been identified if they were addressed and reviewed in isolation.
A 50-person engineering firm based in the Midlands paid a fraudulent £50,000 invoice after attackers accessed and used a recycled password from a 2019 breach list. Dark-web monitoring would have flagged the leaked credential long before the fraud email arrived. Breaches rarely begin with elite exploits. They begin with dull, publicly available scraps that assessments often ignore.
🤝 Selecting a Vendor for CISOs and COOs
If you are thinking of implementing attack surface assessments, here is your checklist for action:
- Define your business-critical assets first so discovery tooling focuses on what really matters and you know which findings to be most concerned about.
- Check their experience confirm that the vendor has a team with appropriate skills and expertise. This may include threat hunters, cyber threat intelligence analysts, penetration testers and architects.
- Confirm coverage review the scope of coverage to ensure all layers of the attack surface are being covered.
- Insist on human validation to cut false positives from reports and provide clear and actionable narrative.
- Require attack-chain modelling to put together the pieces of the puzzle.
🏛️ Frequently Asked Board Questions
We already hold Cyber Essentials Plus, do we need this?
Yes. Cyber Essentials Plus validates baseline controls. Attack-surface work checks if anything outside those controls can still topple you.
Isn’t remediating all this going to take ages?
It really depends on how many findings there are. But findings are presented using a risk focussed approach, allowing you to focus on the closest crocodile to the canoe first.
Will this reduce risk rather than just measure it?
Absolutely. By presenting attack chains and considering the impact of a successful outcome for an attacker, the programme directs limited effort to break the most dangerous chains first, lowering residual risk.
Can’t We Just Google This?
Yes and no. Some of the results uncovered by this reporting can be located (very slowly) through search engines, but not all. Google also won’t be able to put the pieces together into a meaningful attack chain. Search engines are a useful tool in the process, but they are not the whole answer.
How often should we do this?
Some organisations are seeking a continuous assessment approach. This is fine, if you have the resources in place to manage an ongoing influx of findings requiring remediation. If you don’t, this can quickly become overwhelming. We recommend that these assessments are done annually for most organisations, however highly dynamic companies making rapid infrastructure changes may wish to consider a quarterly cycle.
🎯 Conclusion: Shift from Static Compliance to Living Resilience
Traditional attack surface assessments feel safe because they tick an audit box but they rarely dent real-world risk. Attackers evolve and change over time so our visibility must do the same. By adopting an analyst-led approach with threat-intel enrichment and attack-chain storytelling, UK SMBs turn sprawling data into prioritised action that boards understand.
Ready for an assessment that uncovers real risk?
👉 Talk to CyPro’s experts today to get started, and we will be in touch to discuss your Attack Surface Assessment needs.
News and Updates
December 2025
- End-of-year security analysis in December linked multiple 2025 incidents to misconfigurations and temporary access paths that were never captured by traditional attack surface testing, exposing gaps created by routine operational change.
- Year-end reviews by security teams increasingly acknowledged that attack surface testing only reflects risk at a single moment in time, highlighting the need for continuous visibility as organisations plan for 2026.
November 2025
- Industry commentary in November increasingly highlighted how rapid cloud change, short-lived assets and identity sprawl are outpacing traditional attack surface testing, meaning point-in-time assessments are missing exposure that emerges between test cycles.
- Incident response insights shared during the month showed attackers exploiting assets and permissions that were introduced after the last formal test, reinforcing that static testing leaves organisations blind for long periods.
October 2025
- Cyber incidents surged across the UK this month, with the NCSC’s Annual Review 2025 reporting a steep rise in serious attacks and urging organisations to adopt continuous attack simulation and real-time visibility. The findings underline the need for a live understanding of the attack surface instead of relying on static snapshots.
- Microsoft Security followed with an October blog highlighting the growing importance of continuous exposure monitoring to stay ahead of fast-moving threats. The post reinforced that defending modern environments requires constant visibility and validation, not periodic assessments.










